It was nice of Google to inform me. I received this email on June 23
While we were indexing your webpages, we detected that some of your pages were using techniques that are outside our quality guidelines, which can be found here: http://www.google.com/support/webmasters/bin/answer.py?answer=35769&hl=en. This appears to be because your site has been modified by a third party. Typically, the offending party gains access to an insecure directory that has open permissions. Many times, they will upload files or modify existing ones, which then show up as spam in our index.
We detected cloaking on your site and suspect this is the cause. For example at http://weddingbellsblog.com/ we found:
fosamax cheap rx purchase fosamax in eastbay california cheapest generic fosamax online compare fosamax prices find how to use fosamax fosamax for sale cheap 250mg fosamax fosamax 250mg onlineIn order to preserve the quality of our search engine, pages from weddingbellsblog.com are scheduled to be removed temporarily from our search results for at least 30 days.
However when I viewed the source file, I could not find anything. I also checked the templates.
When I typed cialis site:weddingbellsblog.com, 265 pages pertaining to the word came out. I clicked on a cache entry and lo and behold, I saw this on the header:
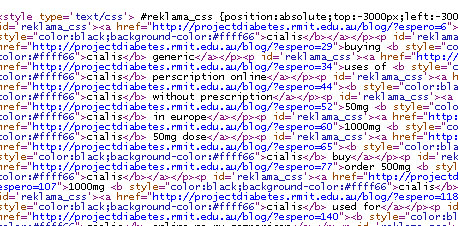
A css code was injected to my template with the id=’reklama_css’
Hundreds of spam links. Checking the templates once more, I could not find anything suspicious. I upgraded to wordpress 2.8 and then got a new template.
Two days later, I still saw the same results. I upgraded the plugins this time.
Then I asked the help of the system administrator of my server (Good thing I own my server), and he found this
we have checked your webroot files for inclusions. Tag with id=’reklama_css’ was found in the following files:
./wp-content/gt-cache/ca/image.php: echo “”.$rmm1.””;
./wp-content/gt-cache/gl/.default.php: echo “”.$rmm1.””;
So, the WP Super Cache was the culprit. I had the old version. The current version was Version: 0.9.4.3. One thing that surprised me is that the wp-content/cache folder was renamed to wp-content/g-cache. I instructed the tech guy to remove the g-cache folder because I didn’t have permissions to delete the folder.
Maybe the hacking was due to other factors other than a vulnerable wordpress plugin. It could have been a combination of an outdated wordpress, a writable folder and the vulnerability of wordpress plugin. It teaches me to always do regular upgrade.
Google is now processing my request for reconsideration.
2 thoughts on “Removal from Google’s Index Due to Hacked WordPress Plugin”
Thanks for sharing this. You are indeed blessed to know these things.
This is scary. I had problems with my blogs about a month ago, never did I thought something like this could happen.
Wow, its great to think how other people minds could work to inject these codes without you knowing it, but its such a sad situation 🙁
.-= Babsy´s last blog ..EJ Baptismal and Friends Meet =-.